VeroLink Installation Guide - for on Premises AD
This guide discusses how to prepare your environment for integration with the VeroGuard Patform.
About VeroLink
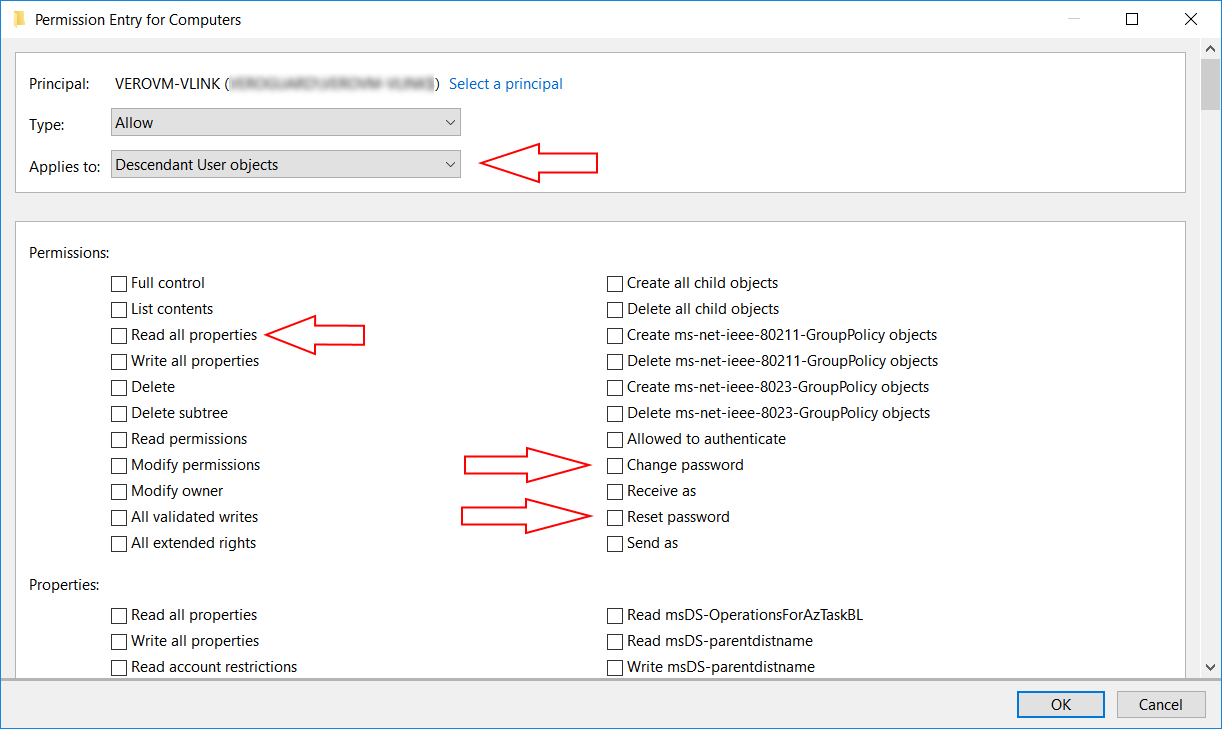
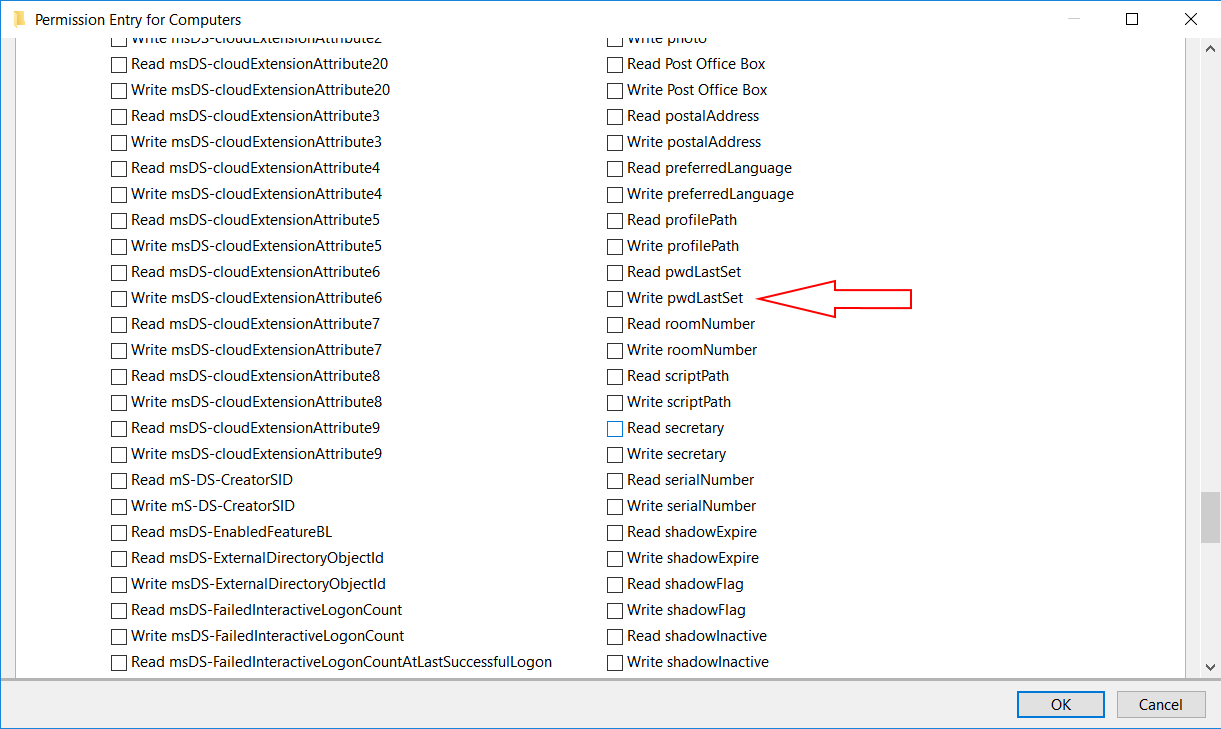
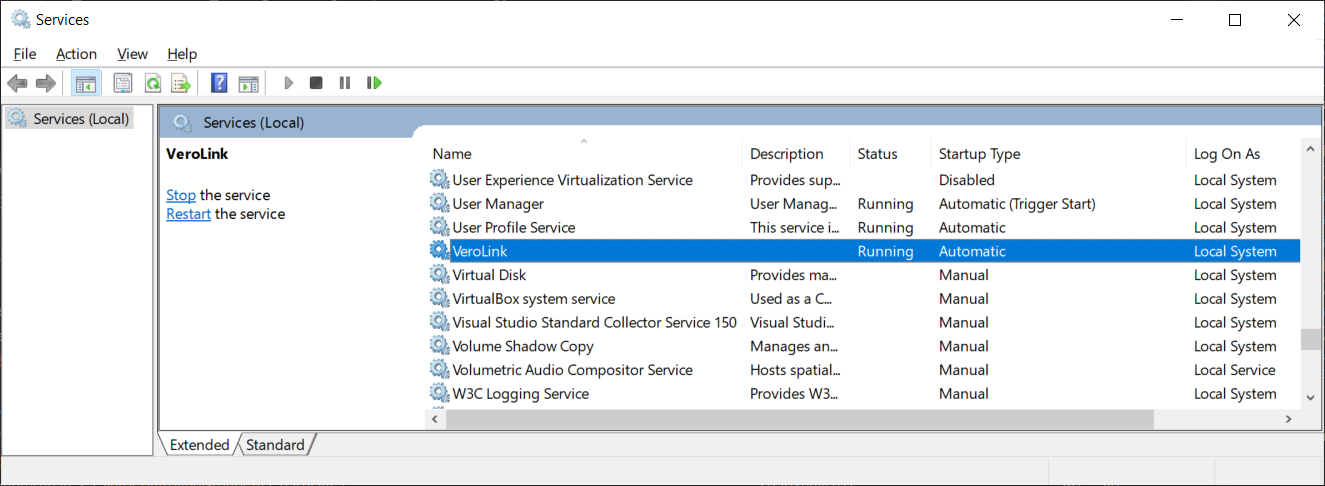
VeroLink is a .net core application designed to support VeroCard's access to Active Directory (AD) services. VeroLink is configured to run as a Windows service on the Microsoft Windows 10 (or higher) or Microsoft Windows Server 2016 (or higher) operating systems. To work properly, the VeroLink machine must be a part of the client's domain and have access to the client's Active Directory. Interacting with Active Directory, VeroLink (on behalf of the user) performs two main operations:
Changes the user's password to a complex totally random 19-character string, and
Obtains user account data.
Once VeroLink is up and running, it tries to establish a connection to the VeroGuard server and remains connected indefinitely until its connection is terminated. If the connection is lost, VeroLink tries to reconnect the VeroGuard server.
Initial checks
Before starting, ensure that your environment meets with the following minimum requirements.
A Domain Controller running Windows Server 2016 or higher.
An Active Directory Domain Services (AD DS) environment, with or without Active Directory Federation Services (AD FS).
An active internet connection; and
Make sure you have obtained the Initial Client Secret from VeroGuard. If you have not received the Initial Client Secret, email the Support team at support@veroguard.com.
Implementation Overview
This guide will take you through the following steps:
Note: Entra or Azure Active Directory Domain Services is not supported by VeroLink.
For setup an integraton with Entra please see XXXX
Final Step
Initial encryption occurs the first time the application is launched. An initial configuration file with unencrypted parameters must be provided in the appsetting.Initial.json file. After running the application and encrypting the settings in the appsettings.Production.json file, the original appsettings.Initial.json file is no longer needed for the application and should be moved from the application working folder to any safe location.
Validating the integration
To validate the integration, you will need to Set up a Workstation for use with VeroGuard and complete a login to a one of the User Accounts you added to the VeroControlled Group, using the user’s assigned VeroCard (see the VeroGuard Admin Guide for more information). The User will need to complete their Account Activation before a successful login can be attempted.
Installation of Serenity Login can be completed without impact to the end user even before they have been issued with a VeroCard. Users can click on the “Enter Password Manually” link to enable a password box on the screen instead of the VeroCard selector dropdown.
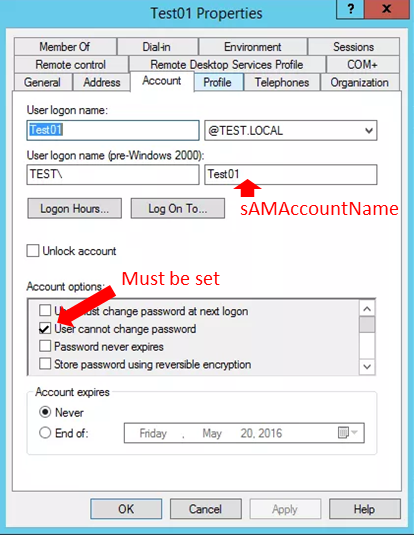
Adding the users to the VeroControlled Group in AD does not impact users (apart from not being able to manually change ther passwords) so can be completed prior to the end user rollout of VeroCards.
On Activation and once they have successfully set their PIN, VeroGuard will take over control of the users account and password. From this point on Users will need to use the VeroCard to access their PC and other integrated applications.
.svg)